Salesforce Trust, Security & Compliance Transformation for a Global Leadership Development Organization

Salesforce Trust, Security & Compliance Transformation for a Global Leadership Development Organization
Introduction
The mandate was simple but non-negotiable: strengthen trust in a platform that powers student enrollment, corporate engagements, and partner programs worldwide. The organization—an established provider of leadership education and professional development—relied on Salesforce as a system of record and coordination hub. Over time, rapid growth, program expansions, and well-intentioned admin changes had left the org with configuration drift, access sprawl concerns, and a manual backup routine that was operationally risky and auditor-unfriendly.
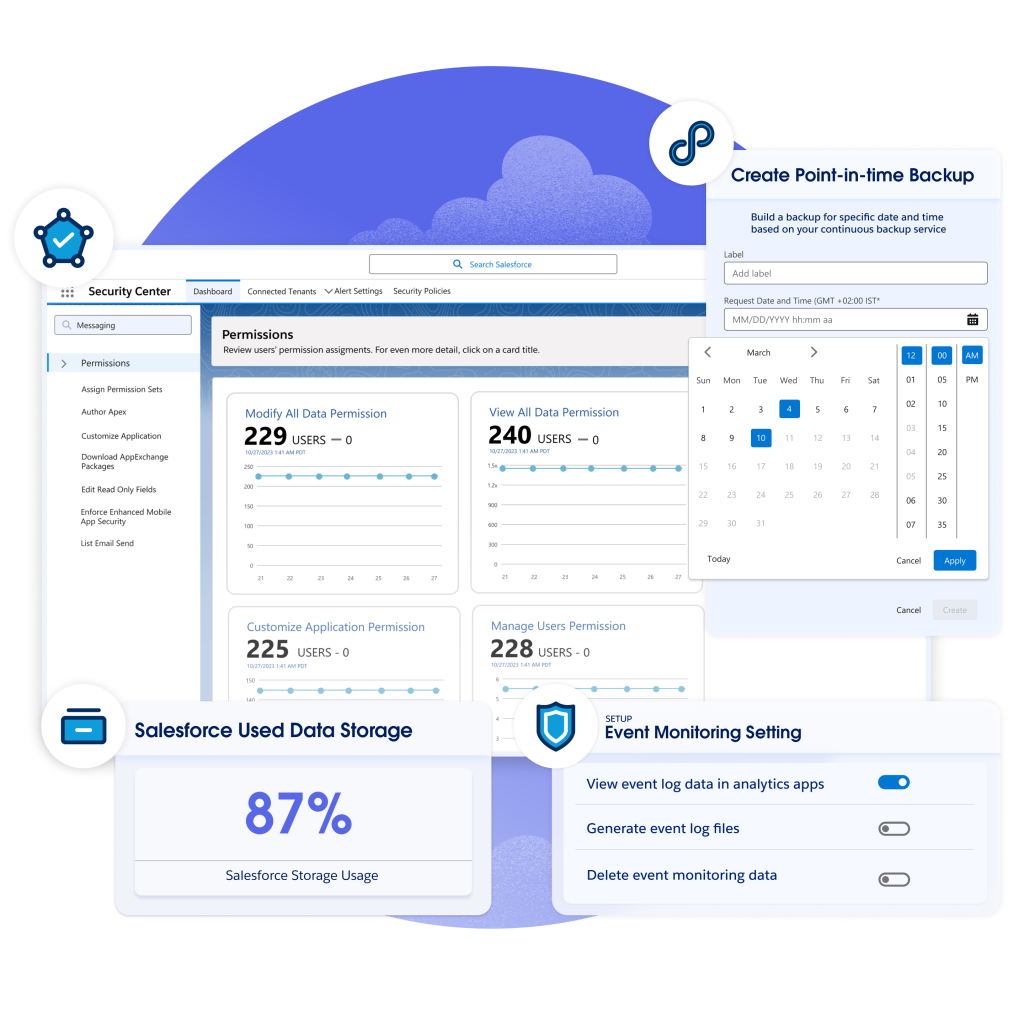
MLVeda’s brief was to raise the Salesforce security posture to a policy-aligned baseline, confirm that access paths reflected least-privilege principles, and move the client from “files in ZIP archives” to a documented, testable backup and disaster recovery (DR) plan. We did this in weeks, not quarters—elevating the Health Check score into the mid-90s from a sub-70 baseline, validating RBAC design across roles, profiles, and permission sets, and delivering a DR runbook and vendor shortlist that compress recovery objectives from weekly/monthly windows to hours after adoption. The result is a more defensible posture, less operational anxiety, and clearer evidence for auditors—achieved with minimal friction to the enrollment, coaching, and enterprise-partnership teams that keep revenue flowing.




Business Challenges
As the organization scaled globally, four intertwined risks emerged.
- Configuration drift and baseline gaps.
The Health Check baseline had fallen behind Salesforce’s recommended standards. Password, session, and transport settings didn’t uniformly reflect current guidance, and accumulated exceptions muddied the control surface. Leaders were asked to “trust the org,” but no one could point to a single, authoritative map of what was enforced and why. - Manual backups and ambiguous recovery.
The team relied on Salesforce’s native data export, producing periodic CSVs bundled into ZIP files. This satisfied a “we have files somewhere” mentality but did little to answer the questions that matter in an incident: Which data can we recover, how quickly, and who has the authority to make that call? The approach also left a wide gap between expected recovery time/point objectives (RTO/RPO) and what could be achieved in practice. - Access sprawl and oversharing doubts.
Roles, profiles, and permission sets had grown organically with new programs. Nothing was overtly broken, but administrators had reasonable concerns about “shadow admin” permissions, permissive sharing rules, and whether org-wide defaults truly implemented a least-privilege posture befitting the brand’s global reputation.
The cost of “good enough.”
Inaction isn’t neutral. Weak baselines invite audit findings and force leadership into post-incident spending. Manual backup routines increase the risk that the wrong data is restored too slowly. Access model ambiguity erodes confidence and slows collaboration. All of it ultimately taxes decision velocity—an ironic burden for an organization that teaches leaders how to move with clarity.
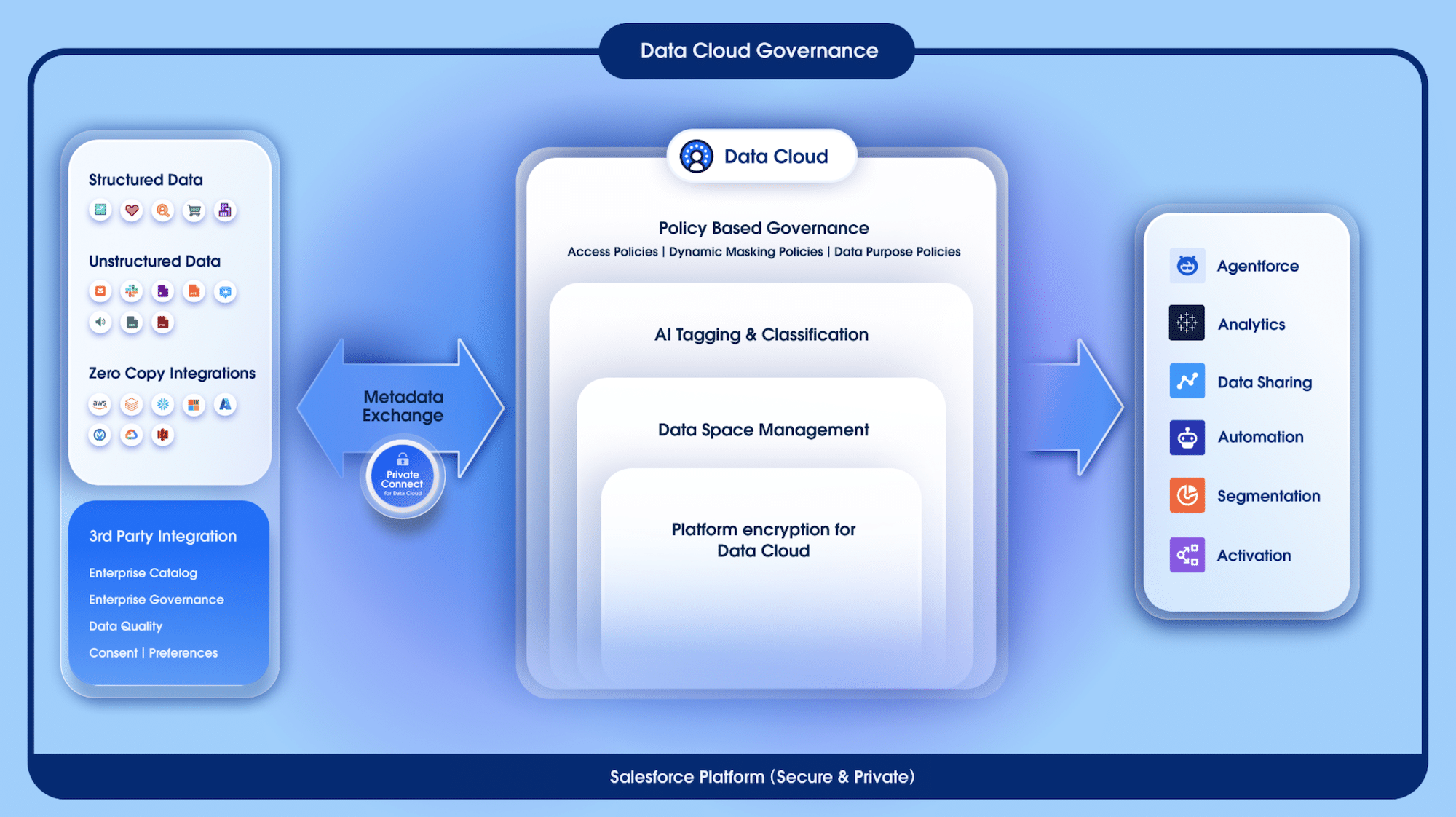
Solution Architecture
We approached the transformation as a sequence of crisp interventions that compound:
- Harden the baseline using Salesforce Health Check, then codify those decisions as policy.
- Validate least-privilege access across profiles, permission sets (and groups), role hierarchy, org-wide defaults, and sharing rules—granting access intentionally, never incidentally.
- Establish DR readiness by defining a runbook, recommending a modern backup solution, and planning a first restore drill—before a crisis demands it.
- Protect business cadence by piloting changes in sandboxes, gating releases, and communicating clearly with program owners.
Architecturally, the work touched four planes:
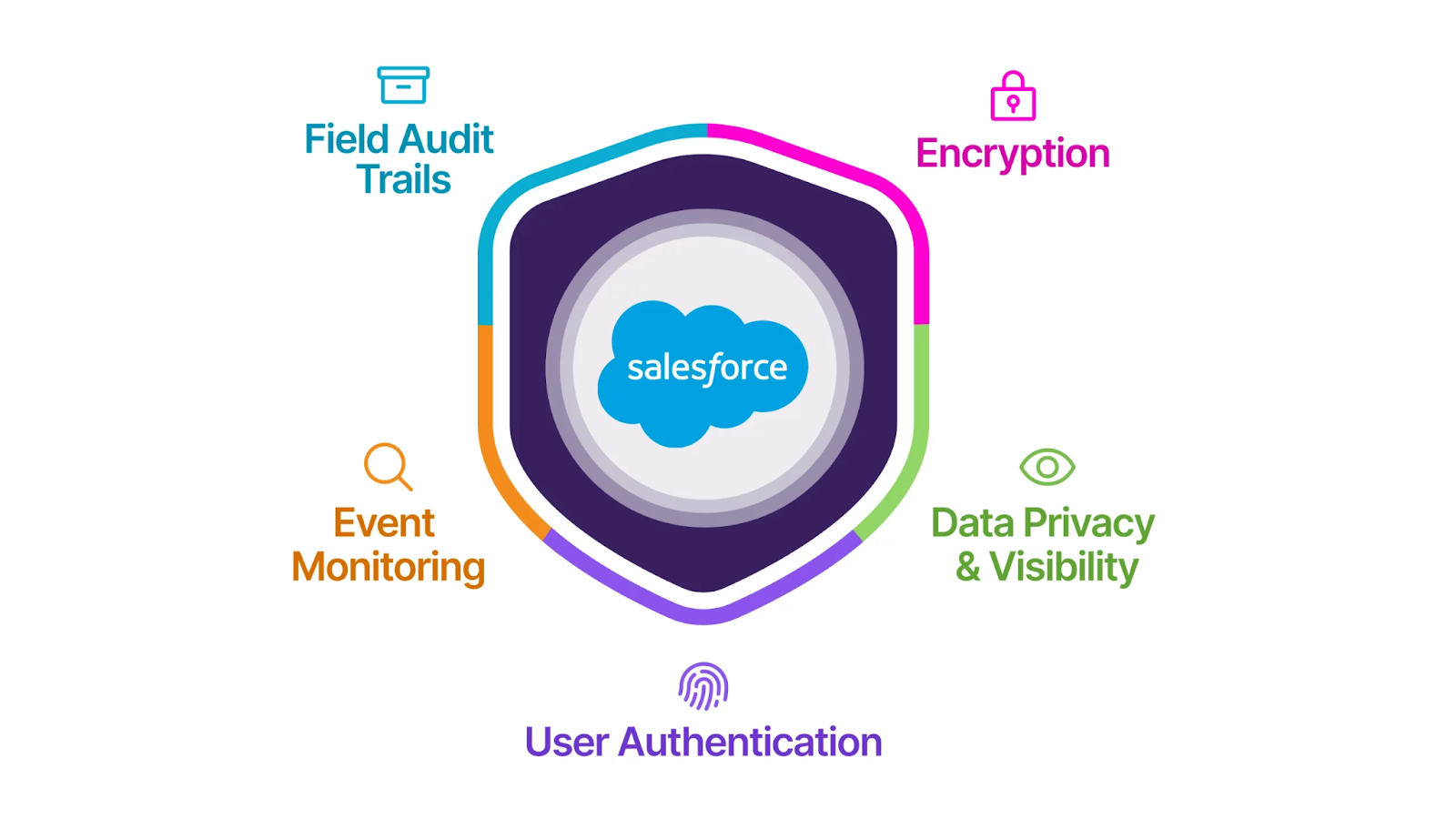
- Security configuration plane. We reconciled password, session, TLS, IP, and content-security settings with Salesforce’s baseline, implemented MFA hygiene checks, and standardized exception handling.
- Access control plane. We rationalized the matrix of profiles and permission sets, verified role hierarchy behaviors against org-wide defaults, and tightened sharing rules to explicitly extend (never restrict) access in known, auditable ways.
- Resilience & recovery plane. We replaced “ZIPs in a drive” with a policy-based backup approach and a DR runbook that defines who does what, in which order, with what evidence.
- Governance plane. We mapped outcomes to recognized frameworks (NIST CSF 2.0; ISO/IEC 27001 Annex A; SOC 2 principles) so the C-suite could translate technical steps into risk-reduction and compliance ROI.
The through-line is pragmatism: leverage native capabilities where strong (Health Check, RBAC primitives), supplement with purpose-built backup/restore where necessary, and keep humans in the loop for governance decisions that require judgment.
Key Technical Components
Security baseline hardening.
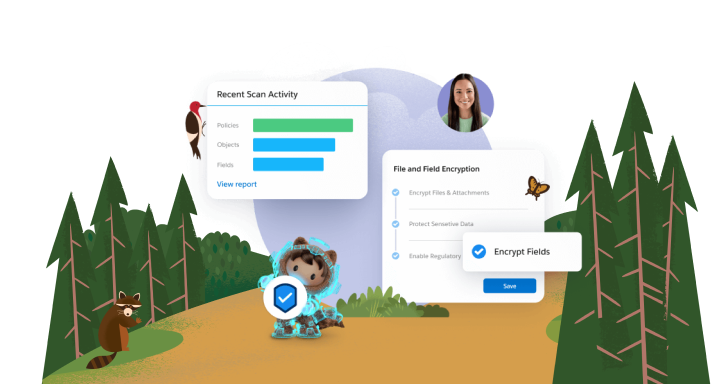
We used Health Check as the organizing lens for remediation. Password complexity and rotation were aligned to policy; session controls enforced timeouts and re-authentication for sensitive operations; transport settings enforced modern TLS while disabling legacy protocols; IP policies and connected app scopes were tightened; clickjacking protections and other content-security measures were standardized. MFA enablement and login hygiene were validated and documented. Importantly, every setting moved from “someone once toggled this” to “we have a reason, a record, and an owner.”
Access governance and least-privilege.
Profiles define the baseline; permission sets (and permission set groups) grant the precise increments needed for each functional role. We inventoried sensitive privileges (e.g., “Modify All Data,” “Manage Users,” “Author Apex”) and ensured they were limited to explicit admin personas. Role hierarchy behaviors were checked against org-wide defaults set to restrictive baselines, and sharing rules were reviewed to confirm they extend access intentionally for collaboration scenarios (not as a workaround for weak defaults). The result is an access model that’s simpler to reason about, easier to audit, and resilient to growth.
Backup and disaster recovery design.
Native data exports are useful but insufficient for rapid, targeted restoration. We documented the current backup cadence and handling risks, then designed a target state centered on policy-based backups (object data, related records, files/attachments), point-in-time restore, metadata coverage, and routine restore testing with evidence capture. A vendor shortlist—including Salesforce’s first-party Backup—was produced with a TCO/feature matrix and an adoption path that minimizes operational disruption.
Governance, observability, and evidence.
Health Check snapshots, access-change approvals, and restore drill artifacts were integrated into an evidence pack. This shifts audit conversations from reactive “hunt and gather” to proactive “here is what’s enforced, why, and how we know it works.” The same artifacts support quarterly leadership reviews and budget justification.
Implementation Methodology
We executed in five phases across eight weeks, balancing pace with operational calm.
Mobilize and baseline (Week 0–1).
We aligned on risk thresholds, change windows, and success criteria with the platform owner and program leaders. Health Check was snapshotted, and a configuration export was prepared for diffing. We compiled an inventory of profiles, permission sets (and groups), roles, org-wide defaults, and sharing rules. Backup routines, export frequency, and storage locations were cataloged, along with the unspoken workarounds teams used to “make it all work.”
Remediate the baseline (Weeks 2–4).
High- and medium-risk findings were remediated in a sandbox, peer-reviewed, and promoted via change sets/DevOps. We piloted login and MFA-related changes with a small cohort to avoid lockouts, verified connected app scopes for third-party tools, and instituted standardized exception processes. Communication emphasized what would change and why—and, crucially, what would not.
Validate and tighten access (Weeks 3–5).
Workshops with business leads translated business roles into permission constructs. We eliminated standing high-risk permissions from non-admin personas, confirmed role hierarchy behaviors matched intent, tuned org-wide defaults to restrictive baselines, and re-authored sharing rules to extend access for specific collaboration patterns. The output was an access governance SOP with a clear request-approval-provision-review loop and a quarterly access review cadence.
Design DR and select a path (Weeks 4–7).
We quantified the RPO/RTO exposure inherent in periodic exports, drafted a DR runbook (incident classification, decision tree, restore workflows, evidence capture, and communications), and produced a vendor shortlist with cost/feature/risk tradeoffs. The executive memo summarized options and recommended a pilot sequence that would culminate in a time-boxed restore drill the following quarter.
Stabilize and handoff (Week 8).
We finalized dashboards (Health Check trend; access review status; backup/DR readiness milestones), consolidated evidence packs, trained admins on the SOPs, and conducted an executive readout. The roadmap included low-regret quick wins (e.g., access-review automation) and informed budget asks (e.g., first-party backup adoption timing).
Throughout, we protected work in progress. No schema changes were introduced that could break enrollment or CRM flows. Releases landed in predictable windows with rollback plans. The implementation felt uneventful by design.
Quantified Business Results
The organization wanted measurable, defensible improvements that a board-level audience would respect. Where precise historical metrics were unavailable, we used conservative benchmarking and made our assumptions explicit.
Realized posture improvements.
- Security baseline uplift: Health Check moved from a sub-70 baseline into the mid-90s after remediation—aligning org settings with Salesforce’s recommended standards and reducing critical misconfigurations to near-zero.
- Access governance confidence: We validated least-privilege across profiles, permission sets, and roles; removed standing high-risk privileges from non-admin users; and established quarterly reviews. Stakeholders now know who can do what—and why.
- Documented DR readiness: A practical runbook exists, ownership is assigned, and a vendor shortlist is approved for pilot. The path from “ZIP archives” to policy-based backup with point-in-time restore is funded and sequenced.
Modeled operational and risk benefits (conservative).
- RPO/RTO compression. Moving from weekly/monthly exports to policy-based backups with point-in-time restore typically reduces RPO from 7–29 days to ≤24 hours and sets RTO goals of ≤4–8 hours for common restoration scenarios. For this organization, that translates into materially lower downtime costs during a data integrity incident.
- Expected loss reduction. Using IBM’s 2025 global average breach cost ($4.44M) as a baseline, we modeled a conservative 15–25% reduction in likelihood/severity attributable to hardened baselines, MFA/login hygiene, and faster containment enabled by clearer access governance and DR. Even at the low end (15%), that yields ~$20k–$35k/year in expected-loss reduction over a three-year horizon ($60k–$105k cumulative), not counting reputational effects.
- Admin time savings. Standardizing backup handling and eliminating manual ZIP orchestration typically frees 10–15 admin hours/month in comparable enterprise orgs. Those hours redeploy to value-add work (automation quality, reporting, enablement).
- Audit-readiness uplift. Evidence packs for Health Check, access approvals, and restore drills shorten audit cycles and reduce findings. While we avoid speculative percentages, prior engagements see audit preparation time cut meaningfully once controls move from ad-hoc to documented SOPs.
ROI view.
The posture uplift and SOPs provided immediate value. DR adoption and the first restore drill—in the quarter following this engagement—unlock the larger step-change. Under conservative assumptions, the initiative pays back within 6–8 months through a blend of reduced incident impact, audit efficiency, and reclaimed admin time.
Strategic Best Practices & Takeaways
Treat Salesforce configuration as a first-class security surface:
Security isn’t only about endpoints and firewalls. In cloud platforms, misaligned org settings are attack surface. Make ≥90–95 Health Check your steady-state target and review deltas quarterly.
Engineer least-privilege with permission sets, not profiles alone:
Profiles establish the baseline; permission sets and permission set groups grant surgical increments aligned to job functions. Inventory and constrain sensitive privileges, validate role hierarchy behavior against restrictive org-wide defaults, and ensure sharing rules are employed to intentionally extend access for known collaboration patterns.
Close the RPO/RTO gap before a crisis forces your hand:
Periodic CSV/ZIP exports are not a DR strategy. Implement a policy-based backup with point-in-time restore and metadata coverage, and schedule restore drills with evidence capture. This is how you turn theoretical recovery into an operational muscle.
Codify changes as SOPs and evidence, not tribal memory:
Write down what matters: login and MFA policies, connected app scopes, access approvals, backup policies, restore procedures. Evidence shortens audits, sharpens accountability, and accelerates leadership decisions.
Speak risk and compliance to unlock budget:
Map remediation steps to NIST CSF 2.0 functions and ISO/IEC 27001 Annex A control themes. This framing translates technical improvements into the language of enterprise risk management and board oversight.
Separate realized from modeled value—and keep both conservative:
Publish the posture uplift and governance artifacts achieved now. Model forward using industry medians for breach cost and backup efficacy. Decision-makers will reward rigor and restraint.
Strategic Conclusion
MLVeda helped a global leadership development organization move from “it works, mostly” to “it’s secure, governed, and recoverable.” In practical terms, that means a Health Check score in the mid-90s, least-privilege access validated and documented, and a clear path from manual exports to policy-driven backup with tested restores. The engagement required no dramatic re-engineering, only discipline and design.
For technology leaders, the takeaway is clear: Salesforce can be made meaningfully more secure and resilient with focused, implementation-aware work. The blueprint is portable—baseline hardening, access validation, DR readiness—and the benefits are cumulative: lower risk, faster audits, greater confidence, and fewer surprises. If your CRM underwrites revenue, donor engagement, or public trust, this is a high-leverage way to protect it.
Next step: MLVeda’s Trust, Security & Compliance Accelerator delivers (1) Health Check hardening to ≥90–95 in 30–45 days, (2) a documented least-privilege access model with SOPs, and (3) DR runbook plus vendor selection and a first restore drill. We’ll meet you where you are—and leave you measurably stronger.
We’re Listening
Whether you're exploring strategic transformation opportunities or seeking a partner to architect and execute enterprise technology initiatives, we're here to help. Reach out to our team at services@mlveda.com or complete the form to begin the conversation.

