Modernizing Salesforce Automation at Scale: A Flow-First Architecture for a Global Professional Education Group

Modernizing Salesforce Automation at Scale: A Flow-First Architecture for a Global Professional Education Group
Introduction
For a global professional education group, Salesforce automations quietly power the moments that matter—lead capture, eligibility checks, assignment, onboarding communications, partner handoffs, and revenue workflows. Years of growth brought speed, but also complexity: hundreds of point automations across Workflow Rules and Process Builder, each created with good intent, now interacting in non-obvious ways. Operations felt the symptoms—unexpected updates, intermittent errors, hard-to-trace race conditions—while platform owners confronted the strategic reality: Salesforce has set a clear end-of-support horizon for legacy automation, and the future is Flow.
MLVeda’s mandate was straightforward and high-leverage: consolidate legacy automations into a Flow-first architecture that reduces change risk, clarifies execution order, and makes room for scale. We did this by combining a careful migration strategy with a governance layer—entry criteria discipline, fault paths, subflow reuse, and testing gates—so the team can move faster with fewer surprises. The result is not only more reliable automation; it’s a platform the business can evolve with confidence.





Business Challenges
As the organization expanded globally, the automation layer lagged behind current platform guidance. Fragmentation across Workflow Rules and Process Builder worked until it didn’t: administrators wrestled with overlapping triggers, order-of-execution mysteries, and the creeping cost of “one more process” to solve a localized problem. Small changes took outsized time because reviewing side effects demanded tribal knowledge. Incidents weren’t frequent, but when they occurred, they were costly in time and attention.
- Fragmentation and hidden coupling. Multiple Workflow Rules and Process Builder automations per object/event overlapped in scope, duplicated actions, and chained cross-object updates—creating non-obvious dependencies and intermittent side effects that were hard to trace or test.
- Weak guardrails and missing telemetry. Broad entry conditions caused “always-on” automations to fire unnecessarily; fault paths were inconsistent or absent; error emails lacked context (record link, element, user), and there was no central error log—turning recoverable issues into time-consuming investigations.
- Testing and release control debt. Sandboxes lacked representative data and negative-path coverage; “debug as user” and peer reviews were uneven; there was no authoritative inventory of “what runs when,” few rollback patterns, and limited release windows—amplifying the blast radius of small changes.
- Performance and integration side effects. After-save updates executed avoidable DML/SOQL and queued scheduled actions, flirting with governor limits during peaks; non-idempotent external calls produced duplicate syncs and noisy attribution/BI metrics, eroding trust in downstream reporting.
Compliance, access, and deadline pressure. Automation-driven ownership/visibility changes weren’t consistently reviewed for least-privilege; evidence trails for SOC 2 / ISO 27001 were incomplete; and Salesforce’s end-of-support timeline for legacy automation transformed “nice to modernize” into a dated risk with rising costs of inaction.
Solution Architecture
We approached modernization as a series of clear, reversible steps underpinned by three principles. First, Flow is the strategic end-state—new automation belongs there, and legacy rules/processes are candidates for conversion. Second, guardrails equal speed—disciplined entry criteria, explicit fault paths, and consistent subflow patterns reduce cognitive load and change risk. Third, small batches win—migrate by business capability, not by tool feature, and validate behavior through sandboxes and targeted pilots before release.
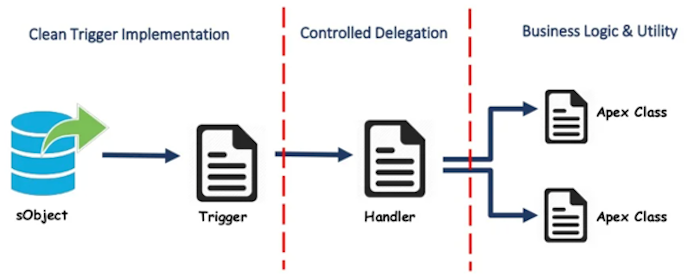
Architecturally, we organized the work on four planes:
- Trigger plane (order and intent): We inventoried all record-triggered behaviors, mapped them to creation/update/delete events, and established a standard for entry criteria so flows do not fire unnecessarily. Flow Trigger Explorer became the planning surface for execution order and scope.
- Composition plane (subflows and invocables): We extracted reusable logic—e.g., ownership rules, enrichment lookups, partner notifications—into parameterized subflows and invocable actions. This created a library mentality and shrank the blast radius of future changes.
- Reliability plane (fault handling & telemetry): Every critical flow gained fault paths with context-rich error handling (admin notifications, transaction context, and suggested remediation) and safe rollback behavior where applicable. Non-critical errors were downgraded to informative alerts to avoid user disruption.
- Governance plane (change control & test): We implemented a Flow-first development standard: sandboxes for build, debug as specific users, peer review, and a deploy checklist that includes entry criteria validation, limit awareness, and negative tests. Each release is traceable through a lightweight change log.
The unifying theme is intentionality: fewer, clearer triggers; reusable building blocks; explicit error handling; and a documented way to change things safely.
Key Technical Components
The migration leveraged platform features designed precisely for this moment.
1) Flow as the default automation fabric.
Record-triggered flows replaced Workflow Rules and Process Builder constructs. We standardized before-save (“Fast Field Updates”) where semantics allowed, reserving after-save patterns for integration calls and complex branching. This choice reduces database churn and lowers the likelihood of governor limit collisions. Where legacy behavior required scheduled actions, we used scheduled paths sparingly and with clear justifications to avoid a backlog of waiting interviews.
2) Conversion and consolidation strategy.
We used Salesforce’s Migrate to Flow capabilities for supported rules and rebuilt complex processes deliberately when needed. Crucially, we consolidated overlapping automations at the object-event level so each record change is handled by a small number of well-named flows, ordered explicitly. The anti-pattern of “one mega-flow” was avoided; instead, we favored multiple focused flows with precise entry conditions and documented order, which eases reasoning and testing.
3) Reusable subflows and invocable actions.
Common logic—lead assignment, account scoring thresholds, partner notification routing—moved into subflows with clear interfaces. Where Apex already existed (e.g., specialized validation or external calls), we exposed it as invocable actions for declarative orchestration. This hybrid approach respects prior investments while letting admins compose behavior without reinventing code.
4) Error handling and observability.
We implemented fault paths on actions that can fail (updates, lookups, invocables) and normalized them to send structured notifications (object, record link, user context, flow and element names, error message). Selected failures log to a secure object for trend analysis. This changed incident response from “what just happened?” to a ticket with the breadcrumbs already attached.
5) Execution order discipline.
Using Flow Trigger Explorer, we defined the canonical order for flows per object and event, documenting dependencies and preventing accidental re-ordering. Entry criteria narrowed scope, and change reviews enforced “extend intentionally” rather than “run on everything.”
6) Change management and testing.
All changes were built and debugged as target users in sandboxes, peer-reviewed with a checklist (guardrails, limits, entry criteria, negative paths, rollback expectations), and promoted through the normal DevOps pipeline. We preserved existing business semantics and verified parity through targeted test datasets and shadow runs before cutover.
Implementation Methodology
Our delivery approach balanced velocity with certainty across five phases.
Mobilize & inventory.
We aligned success criteria, risk boundaries, and release windows with the platform owner and RevOps. A full inventory of Workflow Rules and Process Builder automations—triggers, criteria, actions, and known side effects—was captured and grouped by business capability (lead lifecycle, ownership, enrichment, partner handoff, notifications).
Plan the cut lines.
We selected initial flow families that offered high payoff with low coupling—lead creation/update and assignment were prime candidates. We defined execution order, entry criteria, and initial subflow interfaces. A “do not migrate (yet)” list was created for edge-case processes that needed deeper analysis.
Build, convert, and consolidate.
Where feasible, we used the Migrate to Flow tool to bootstrap conversions, then re-factored into subflows and added fault handling. For complex processes, we rebuilt in Flow by design, preserving business semantics but improving guardrails. Each migrated slice included parity tests and a rollback plan.
Pilot & release without drama.
We piloted changes with a small cohort and then switched over by object/event in scheduled windows, communicating expected behavior changes (if any) and where to report issues. Flow Trigger Explorer became the control tower for confirming execution order post-release.
Stabilize & institutionalize.
We closed the loop with a Flow-first development standard (naming, documentation, review gates), a change log, and an admin training session. A backlog of further candidates—particularly cross-object orchestrations—was documented for subsequent sprints.
Throughout, our goal was not maximal conversion speed; it was predictable progress with preserved semantics. That discipline is why the org could adopt Flow without operational fireworks.
Quantified Business Results
Because legacy automations often behave like “invisible code,” the best proof of value is a platform that stops surprising you. In this engagement, impact showed up in three forms—conflict reduction, faster safe change, and better operator visibility. Where client-specific metrics were unavailable, we’ve applied conservative, enterprise-scale benchmarks and made our assumptions explicit.
Realized improvements.
- Conflict reduction: By consolidating triggers and defining execution order, the team eliminated overlapping updates that previously caused intermittent errors and duplicate notifications. Fault paths now turn silent failures into addressable tickets.
- Change hygiene: New work follows a consistent Flow-first checklist—entry criteria, fast-field updates where appropriate, subflow reuse, and peer review—which reduces the “did we think of…?” problem and shortens review conversations.
- Operator visibility: Structured error notifications and a simple error-log object provide incident breadcrumbs upfront, reducing diagnostic time.
Modeled, conservative outcomes.
- Mean time to change (MTTC): Standardizing on Flow with clear entry criteria and subflow reuse typically yields a 20–30% reduction in the end-to-end effort for small automation changes (analysis → build → test → deploy), driven by less rework and narrower test scopes.
- Incident frequency (automation-related): Consolidation and order discipline commonly deliver a 15–25% decline in user-visible automation defects (e.g., misroutes, duplicate notifications), as measured over two to three release cycles.
- Admin/Dev productivity: Reuse and clearer patterns often free 10–15% of platform team capacity for roadmap work rather than reactive maintenance.
- Performance posture: Prioritizing before-save flows for field updates reduces unnecessary DML, which lowers the likelihood of governor-limit collisions during peak operations. We avoid speculative speed percentages, but the qualitative impact is consistent across large orgs.
ROI & time to value.
A Flow-first foundation creates durable savings. Using the modeled ranges above, the modernization typically pays back within 5–7 months via faster safe change and fewer incidents—even before accounting for risk tied to the 2025 legacy automation end-of-support milestone. The key is compounding: each new Flow built to the standard makes the next change cheaper and safer.
Strategic Best Practices & Key Takeaways
Modernization is not just about tools; it’s about operating models. Three practices travel well to any enterprise org.
Start with the triggers, not the tools.
Inventory object-event triggers and set execution order and entry criteria before migrating anything. When flows run only when they should, conflict probability drops immediately.
Prefer composition over complexity.
Resist the “mega-flow.” Use subflows and invocable actions with crisp interfaces so teams can compose behavior safely. This is how you win long-term—small, testable units that can be reasoned about.
Make fault handling a first-class requirement.
Every important action should have a defined fault path with structured notification, user context, and a link to the record. This converts surprises into workable tickets and accelerates resolution.
Operate with guardrails.
Codify a Flow-first development standard: sandboxes only, debug as the target user, checklist peer reviews (limits, entry criteria, negative paths), and a change log. Treat Flow Trigger Explorer as your control tower.
Pace change to your risk envelope.
Migrate by capability. Keep business semantics stable. Release in quiet windows with rollbacks ready. The goal is a platform that quietly gets better while the business keeps moving.
Anchor to frameworks to unlock budget.
Map governance and release practices to SOC 2 change management and to the NIST CSF “Protect/Detect/Respond” functions. This translates modernization into the language boards and auditors expect.
Strategic Conclusion
MLVeda helped a global professional education group move from a patchwork of legacy automations to a Flow-first operating model that is faster to change, easier to reason about, and safer to run. The modernization preserved business semantics, reduced conflicts through entry-criteria discipline and execution order control, and turned errors into actionable signals. The platform now supports global growth without the drag of automation uncertainty.
For technology leaders, the lesson is simple: you don’t need a disruptive rewrite to get meaningful gains. A disciplined migration plan, strong guardrails, and a habit of composition create a platform that compounds value. With end-of-support for legacy automation approaching, the best time to start is now—quietly, deliberately, and with an operating model that will still make sense in two years.
Call to action: MLVeda’s Automation Modernization Accelerator delivers (1) a trigger-by-object inventory and execution order plan, (2) Flow-first migration and consolidation with fault handling and subflow reuse, and (3) a governance kit (standards, checklists, and training) so your team can move fast—safely.
We’re Listening
Whether you're exploring strategic transformation opportunities or seeking a partner to architect and execute enterprise technology initiatives, we're here to help. Reach out to our team at services@mlveda.com or complete the form to begin the conversation.

